Security experts at ESET have released the final two parts of their new research into the operations of the notorious Sednit hacking group which – as previously discussed – has targeted over 1000 high-profile individuals with phishing attacks and zero-day exploits.
The Sednit gang, also known as APT28, Fancy Bear, Pawn Storm and Sofacy, are highly experienced, and have been engaged in criminal activity since at least 2004. They have developed sophisticated attacks that bypass the typical network security at compromised organizations.
In parts two and three of their research, entitled En Route with Sednit: Observing the Comings and Goings and En Route with Sednit: A Mysterious Downloader respectively ESET's threat analysts have taken a closer look at the software used by Sednit to spy on its targets and steal confidential information.
Sednit's espionage toolkit is only deployed on targets deemed interesting to the hacking group after a period of reconnaissance.
The toolkit has three main components, made up of two spying backdoors (SEDRECO and XAGENT), and a network tool named XTUNNEL.
SEDRECO and XAGENT spying backdoors
Why have two backdoors to spy upon your victims rather than just one? Well, the explanation – according to ESET's research team – is fairly straightforward: "Deploying both spying backdoors at the same time allows them to remain in contact if one of them becomes detected."
Once in place, the SEDRECO backdoor trojan provides its remote operators with a variety of functions - including the ability to read and write files, turn on keylogging to furtively capture a user's keypresses (and no doubt passwords), scour the victim computer's hard drives and map network resources.
ESET's research has further discovered that SEDRECO contains the capability to run external plugins, downloaded and executed as requested by a command-and-control (C&C) server under the hackers' control.
A SEDRECO plugin identified by the researchers was found to share code with a module used by XAGENT, the other backdoor utilized by the Sednit gang.
XAGENT can exfiltrate information from compromised computers via HTTP and email, working alongside other components in the toolkit including USBSTEALER, which attempts to steal data from air-gapped computers. During their investigations, ESET researchers were able to retrieve the complete Xagent source code intended to work under GNU/Linux operating system.
Partial directory listing of Xagent source files
Versions of XAGENT are known to have been actively used by the gang from November 2012 to the present day, counting amongst its victims the infected computers at the Democratic National Committee (DNC), the governing body of the US Democratic Party.
Although versions of XAGENT have been seen for Windows, Linux and iOS, ESET's team of researchers believe that it would be surprising if there has not also been a version of XAGENT created for other operating systems, including Android.
The well-designed XAGENT malware is comprised of a series of modules providing varying functionalities, and the samples examined by ESET's researchers indicate that the Sednit hacking gang adapts each attack for specific targets. This also, of course, avoids the risk of exposing all of XAGENT's code to security researchers.
XTUNNEL
Finally we come to XTUNNEL, the network proxy tool used by the Sednit group to relay network traffic between a C&C server on the internet and infected computers on their local networks.
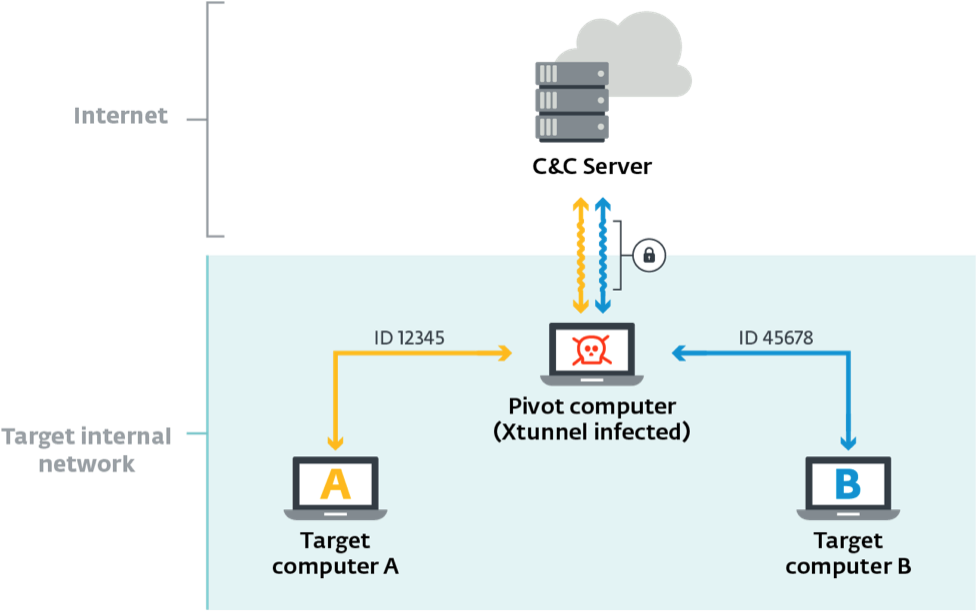
The first known sample of XTUNNEL dates from May 2013, and later versions were found on servers operated by the Democratic National Committee's in May 2016, and by the German
parliament in June 2015, and the code has continued to be developed since then.
The researchers say that significant resources have been put into the development of XTUNNEL, SEDRECO and XAGENT, as they describe in En Route with Sednit: Observing the Comings and Goings:
"In order to perform its espionage activities, the Sednit group mainly relies on two backdoors, Xagent and Sedreco, which were intensively developed over the past years. Similarly, notable effort has been invested into Xtunnel, in order to pivot in a stealthy way. Overall, these three applications should be a primary focus to anyone wanting to understand and detect the Sednit group’s activities."
However, it would be a mistake to think that these are the only weapons up Sednit's arsenal. For instance, targeted computers are regularly put at risk by password retrieval tools, some of which are custom-made for particular attacks, and tools that grab screenshots.
DOWNDELPH - A mysterious downloader
The final focus of ESET researchers' deep dive in the Sednit group is a special downloader called DOWNDELPH.
DOWNDELPH, which gets its name from being written in the Delphi programming language, is used in hacks orchestrated by the Sednit group to deploy the previously mentioned XAGENT and SEDRECO onto infected computers.
In at least one case examined by ESET, DOWNDELPH was delivered via a booby-trapped Word document sent in a targeted attack to users, posing as an invitation to a conference about Russia-Ukraine relations in the wake of the shooting down of Malaysian aircraft MH17.

Once in place, DOWNDELPH downloads a configuration file from the internet, and fetches payloads from a series of command & control (C&C) servers.
But perhaps most interestingly, DOWNDELPH has only been used seven times over the past two years according to the telemetry data collected by ESET's researchers.
And, on a few occasions, it has been deployed alongside a never documented Windows rootkit and bootkit (which curiously shares some of its code with the infamous BlackEnergy malware linked to attacks on Ukrainian energy distribution companies.)
The use of rootkit/bootkit technology to hide the activities of the Sednit group and the small number of deployments suggests one thing: this group of attackers wanted to do everything they could to avoid being noticed.
Sometimes, in the world of global hacking, the intention is not to make as much money as you can as fast as you can, but instead to play the long game - lying unseen for years, secretly stealing information without the knowledge of innocent victims.
If you're interested in finding out much more, be sure to read the latest technical papers published by ESET's research team:
- Part one: En Route with Sednit: Approaching the Target. (where ESET researchers describe the typical targets of the Sednit group, and the typical techniques used to compromise targeted systems).
- Part two: En Route with Sednit: Observing the Comings and Goings.
- Part three: En Route with Sednit: A Mysterious Downloader
You can download the whole Sednit whitepaper here and you can also find Sednit-related IOCs on ESET’s Github account. For any inquiries related to the white paper, contact its authors at: threatintel@eset.com




